Ingress Introduction
Ingress exposes HTTP and HTTPS routes from outside the cluster to services within the cluster. Traffic routing is controlled by rules defined on the Ingress resource.
Here is a simple example where an Ingress sends all its traffic to one Service:
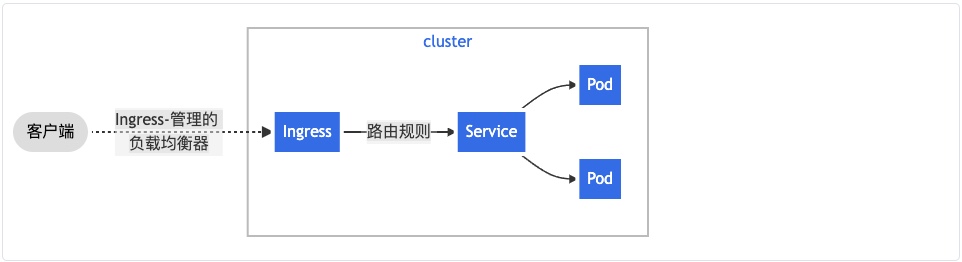
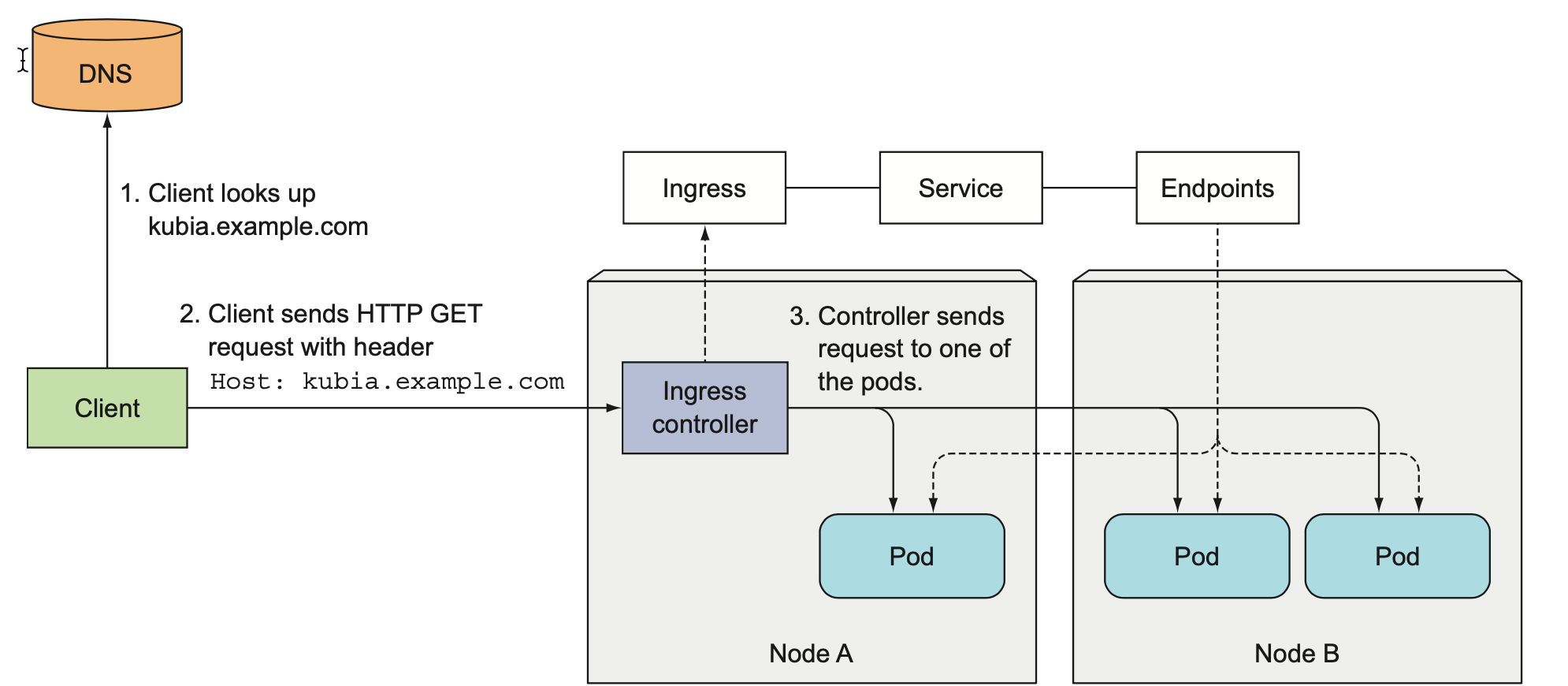
Figure below shows how the client connected to one of the pods through the Ingress controller. The client first performed a DNS lookup of kubia.example.com, and the DNS server (or the local operating system) returned the IP of the Ingress controller. The client then sent an HTTP request to the Ingress controller and specified kubia.example.com in the Host header. From that header, the controller determined which service the client is trying to access, looked up the pod IPs through the End- points object associated with the service, and forwarded the client’s request to one of the pods. As you can see, the Ingress controller didn’t forward the request to the service. It only used it to select a pod. Most, if not all, controllers work like this.
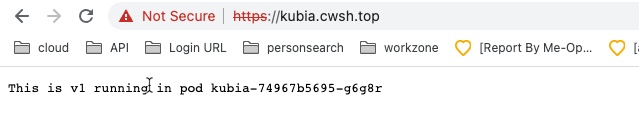
Test ENV
- Bandwangon host Ubuntu 18.04 LTS
- k8s versoin v1.20.4
- setup k8s in Bandwangon host, guide: https://wilsoncai.top/2021/11/28/k8s-Installation/
Install ingress-nginx
# change is following: https://www.cnblogs.com/koala2020/p/15195450.html
k apply -f https://raw.githubusercontent.com/caiwenhn2008/k8s-library/main/deploy.yaml
install sample service and deployment
k create -f https://github.com/caiwenhn2008/k8s-library/blob/main/kubia-svc.yaml
k create -f https://github.com/caiwenhn2008/k8s-library/blob/main/kubia-deployment-v1.yaml
install ingress for sample service
k create -f kubia-ingress.yaml
kubia-ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: kubia
spec:
tls:
- hosts:
- kubia.cwsh.top
secretName: tls-secret
rules:
- host: kubia.cwsh.top
http:
paths:
- path: /
backend:
serviceName: kubia
servicePort: 80
generate tls CERTIFICATE
openssl genrsa -out tls.key 2048
#change kubia.cwsh.top to your actual host, it could *kubia*.cwsh.top if you want the CERTIFICATE support all sub domains
openssl req -new -x509 -key tls.key -out tls.cert -days 360 -subj /CN=kubia.cwsh.top
install secret
kubectl create secret tls tls-secret --cert=tls.cert --key=tls.key
add your sub domain
my DNS is setup in aliclound
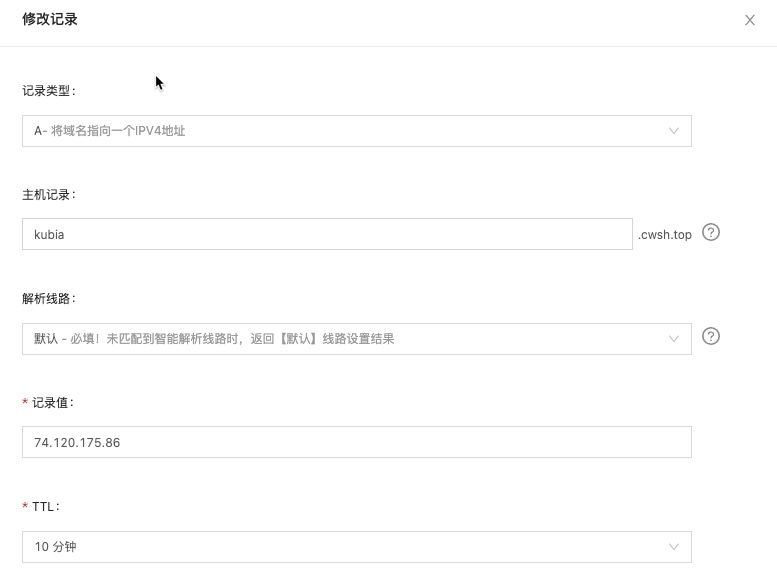
that’s it, we could access service via ingress now